Data loss prevention (DLP)
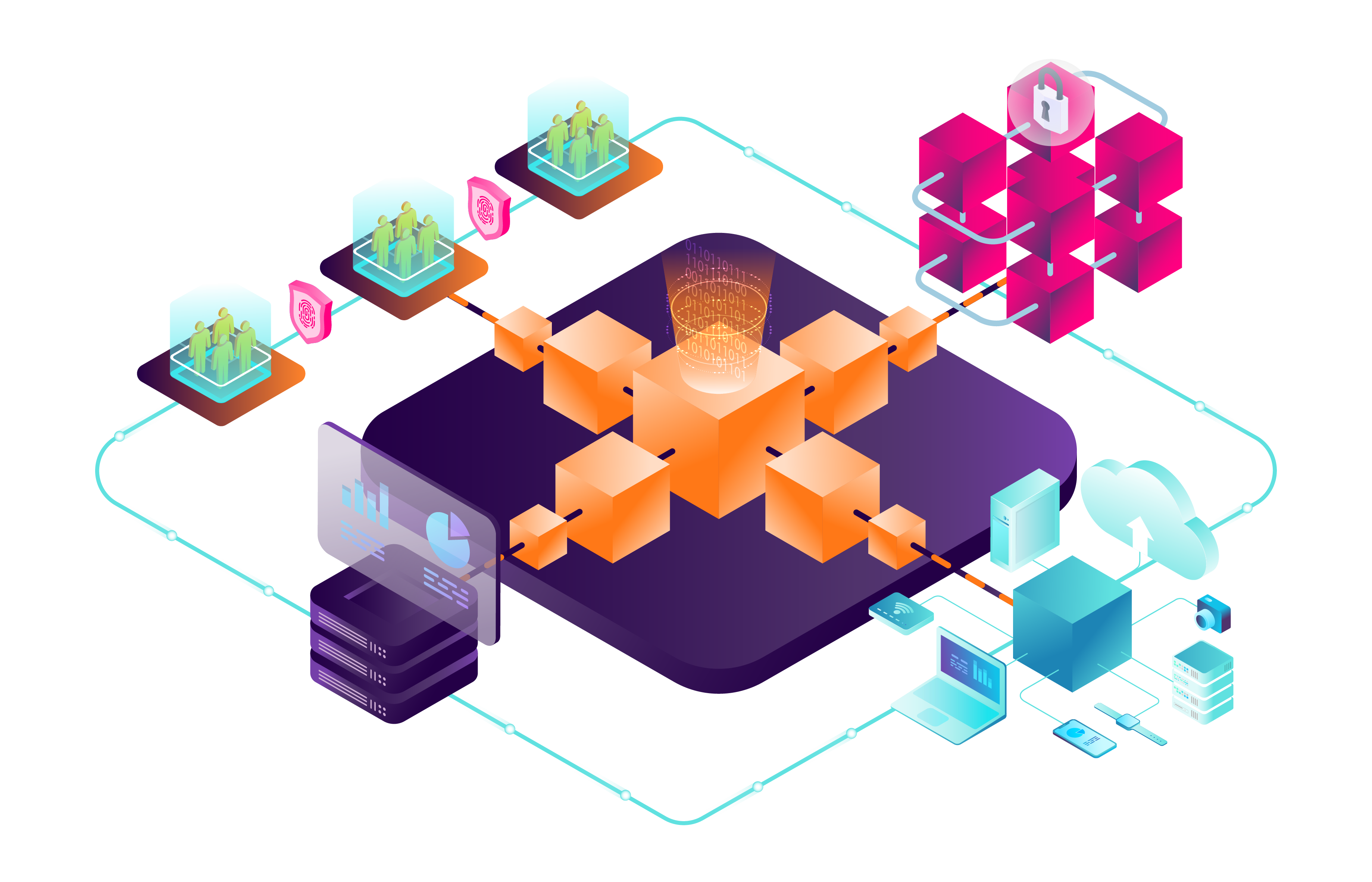
LogLocker provides irrefutable tracking and auditing of actions on documents or files that support data loss prevention.
Enhancing DLP across the file and document lifecycle
Data Loss Prevention (DLP) continues to be a significant challenge for organisations. This is due to the complexity and volume of data being generated. Combined with the diversity of data this makes it difficult for organisations to protect all sensitive data. When factoring in the volume of data, and its exponential growth, it's not surprising that organisations are finding it difficult to monitor and protect the data they are custodians of.
DLP challenges
Compliance professionals face a number of problems in tackling data loss:
- Sophisticated cyber attacks. Attackers constantly develop new methods for stealing data.
- The human factor. Employees can accidentally or intentionally expose sensitive data.
- The need for flexibility. Businesses need DLP solutions that adapt to changing business needs and new technologies.
Irrefutable tracking and audit

Identify sensitive documents
LogLocker can identify sensitive documents being created, shared, or accessed by tracking actions on documents. This information can be used to create policies and rules that protect these documents.

Monitor document access
LogLocker tracks who accesses sensitive documents and what they do with them. This information can be used to identify suspicious activity, such as employees downloading sensitive documents or sharing them with unauthorised users.

Prevent unauthorised access
LogLocker can use the information collected about document access to identify and prevent unauthorised users from accessing sensitive documents.

Investigate incidents
If a data loss incident occurs, the investigating team can use LogLocker and the information collected about document access to investigate the incident and identify the responsible party.
The actions LogLocker can track and record
By tracking who is accessing, sharing, and using sensitive documents, LogLocker protects them from unauthorized access and use. Whether it is contractual information, intellectual property, or 3rd party information, LogLocker tracks and creates a trusted, irrefutable, secure audit of the event and actions taken through the data lifecycle.
Database access
LogLocker tracks who is accessing a database and what they do with it. This is used to identify suspicious activity, such as a user downloading a customer database or sharing it with an unauthorised user.

Email tracking
LogLocker tracks who sends emails with sensitive information, such as trade secrets or customer data. This information is used to prevent unauthorised users from sending emails with sensitive information.

Printing documents
LogLocker tracks who is printing sensitive documents, such as financial reports or customer contracts. This information is to prevent unauthorised users from printing sensitive documents.
Explore LogLocker in the company of a blockchain expert
Get a free demo and discover how to improve your compliance data audit, investigation and reporting.