Protect and build business trust
Traditional archiving tools are no longer enough to defend compliance and make your business AI ready - they're costly, complex and hard to query.
For a fraction of the cost, LogLocker provides a searchable, immutable, long-term record of logs, data and events.
Cost-effective, long-term data archiving
Quick to deploy, simple to search, and easy to manage, LogLocker enhances Sentinel, making it a powerful tool for compliance.
Wonder why you keep so much log data? LogLocker eliminates inefficiency by using automations to selecting only the logs you need. This reduces the cost, volume and complexity of log storage.
No fuss integration
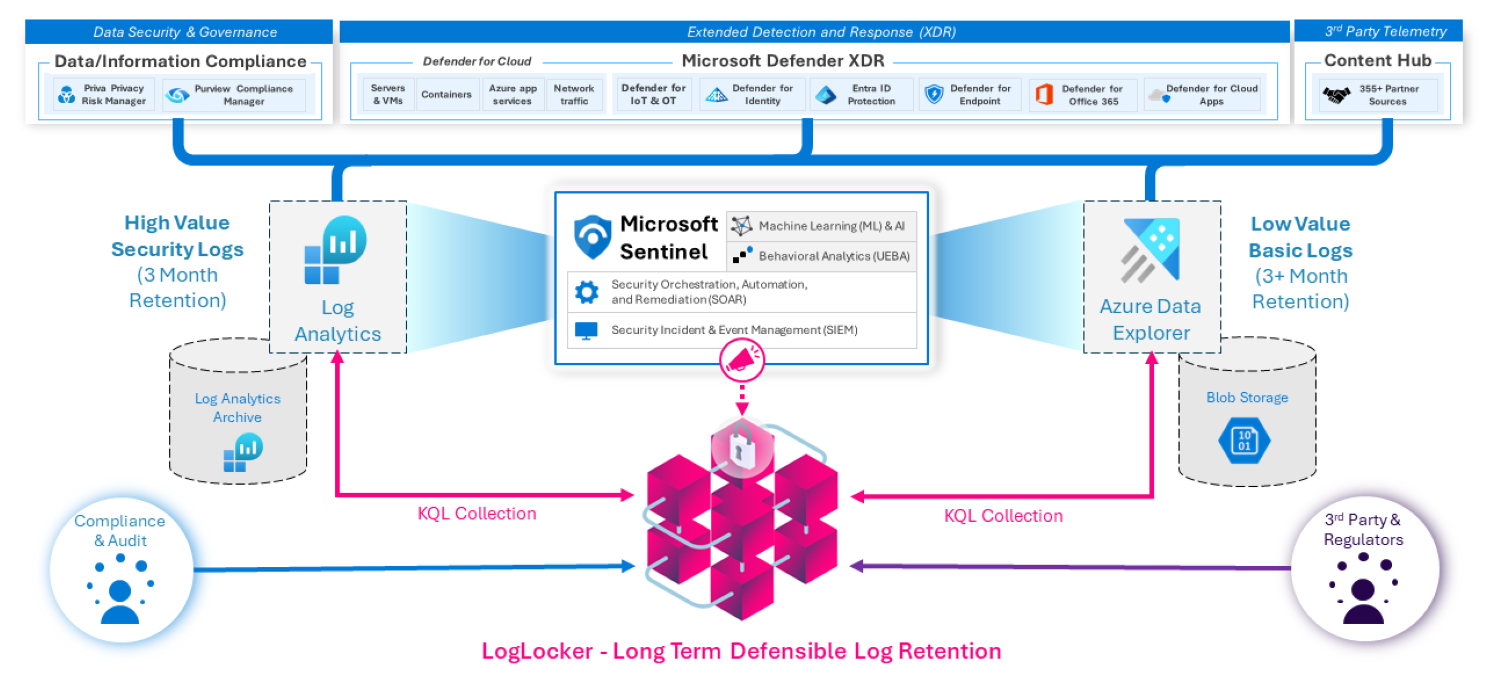
LogLocker integrates into the native features of Microsoft Sentinel, Log Analytics and Azure Data Explorer (ADX), so your logs can be filtered, collected, and archived.
Immutable, long-term retention
LogLocker is the only low-cost, long-term data preservation and retention solution designed specifically for Microsoft Sentinel log data.

Extend the value of Sentinel logs
LogLocker enhances your investment, enabling compliance teams to use valuable Microsoft Sentinel logs for investigations and information requests.

Instant search and retrieval
Instant search and retrieval eliminates the time and effort required to run complex queries. Secure data exchange tools allow selected data and insights to be easily shared.
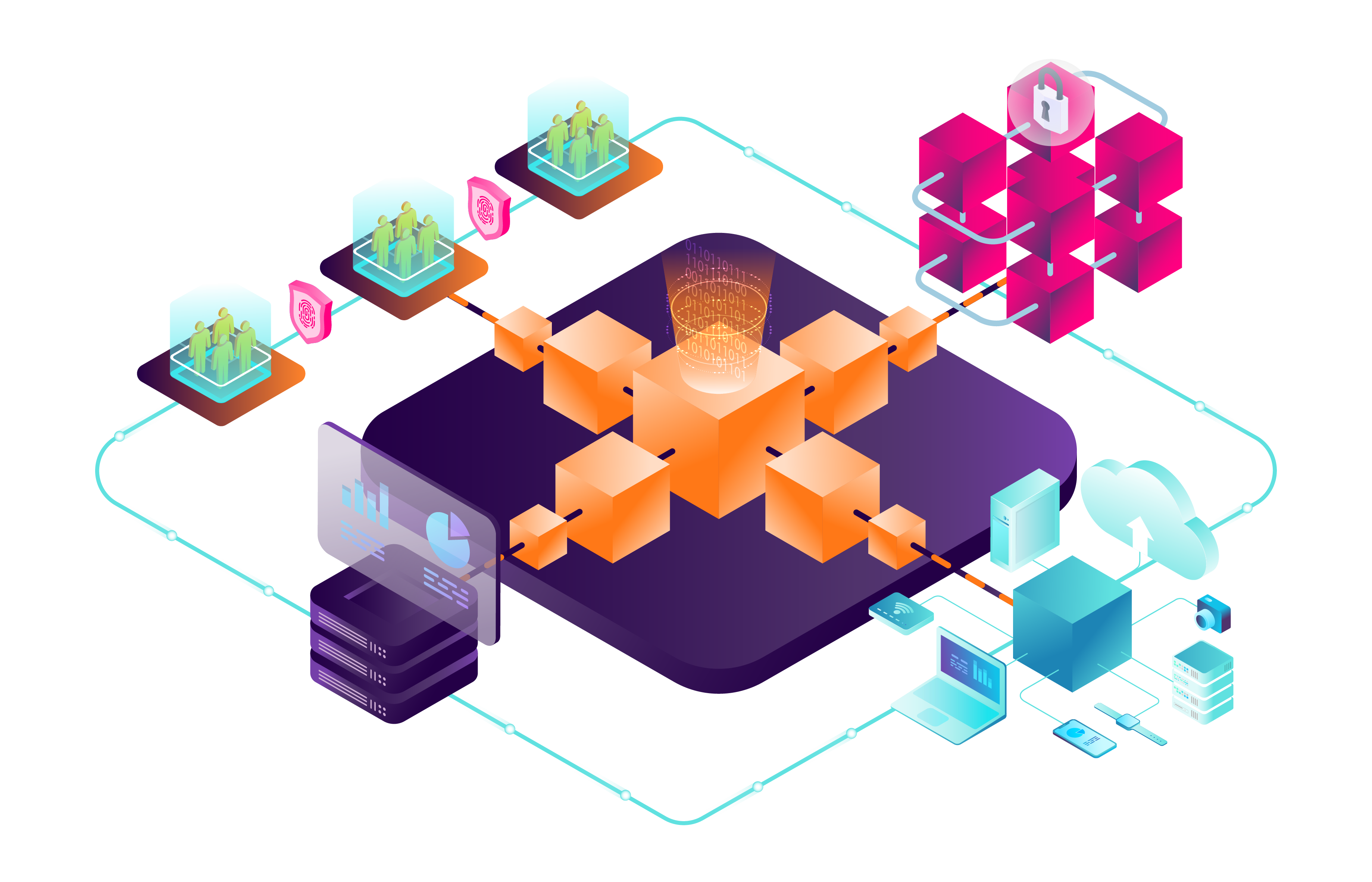
A single pane of glass for 140 Microsoft Sentinel data sources
Microsoft Sentinel provides a unique opportunity for Information Security teams to harvest event and log data from security insights and sensitive data signals from over 140+ published application connectors. Using KQL queries, playbooks and automation, InfoSec teams can select and collect event data to support compliance and security initiatives where long-term retention is required.

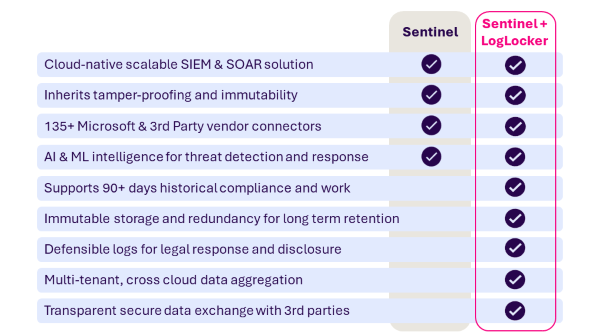
Enhance Microsoft Sentinel with long-term data retention
Integrating Sentinel with LogLocker transforms live security analytics and threat intelligence into long-term, easy-to-retrieve activity records that protect your business.
Explore LogLocker in the company of a blockchain expert
Get a free demo and discover how to improve your compliance data audit, investigation and reporting.