Retain and preserve high-value logs with ease
Act now to simplify and rationalise the management of your logs with LogLocker for Microsoft Sentinel.

.png)
Make Microsoft Sentinel a crucial component for compliance, just like it is for security
- Want more from your Microsoft Sentinel investment?
- Let down by compliance tools lacking legal defence details?
- Struggling with the surge in telemetry data?
- Business demanding longer log data retention?
- Concerned logs aren't managed or preserved effectively?
LogLocker tackles these challenges for Microsoft Azure and Sentinel users, reducing costs, minimising data and protect the logs you need.
LogLocker solves compliance challenges by providing a robust log management platform for the data and AI economy
Never has it been more important to retain only the necessary log data to reduce cost and storage complexity - if you retain logs for long periods its essential data lineage is preserved to ensure legal defensibility.
Reduce cost
Shocked at the limited options and long-term cost of retaining your logs? Implement a cost-effective alternative to Log Analytics and Azure Data Explorer archiving
Minimise data
Looking for a way to avoid storing all logs? Only archive and retain the specific logs you need for business requirements and compliance
Preserve logs
Worried your logs are not given enough protection? Preserve and protect logs using distributed ledger technology for truly defensible legal evidence.
Ready for integration
LogLocker API's were designed for easy and effective integrations with Microsoft Sentinel, Log Analytics, Azure Data Explorer and other Microsoft services.
No retraining
LogLocker uses Kusto Query Language (KQL) to define the targeted log collections via Azure Sentinel allowing it to align to existing staff roles and skills.
Extensible data sources
Want to bring in other data sources? No problem. LogLocker will work with any volume or type of data, log or query.
Where is LogLocker installed?
Installed on Azure
The LogLocker platform is deployed into your Azure subscription so you govern the security and location of your data using the configuration option provided. Includes Terraform, Kubernetes, Storage and Logic App.
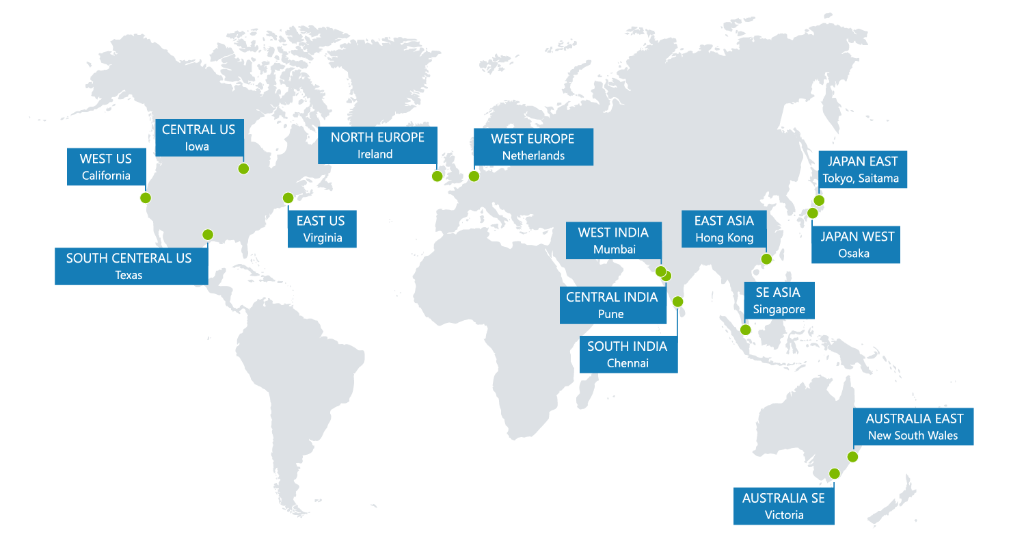
In any Azure region
LogLocker can be deployed into any Azure region ensuring your data is stored on the blockchain network that respects your data sovereignty requirements

Azure Blob storage options
Larger data sets can extend to off-chain storage using Azure Blob storage. Further options for multi cloud storage are also available.
How does LogLocker work?

Targeted protection
Target the specific logs you want to capture using KQL queries run from Sentinel against Log Analytics and Azure Data Explorer. Then add the LogLocker automation to the query workbook.

Sentinel triggers
When a Sentinel alert is triggered, LogLocker will request the KQL and run the specific query against either the Log Analytics Sentinel workspace or Azure Data Explorer (ADX).
Stored logs
Only the logs you specify are stored and preserved in LogLocker, ready for search, sharing and review.
Business
from $2850/mo
Best for smaller log volumes. Retain and manage your high-value logs quickly and easily
-
Single tenant
-
Sentinel connector
-
Private blockchain
-
On-chain storage
-
Elastic search
Enterprise
from $5200/mo
All the Business plan features plus off-chain storage for larger log volumes
-
Single tenant
-
Sentinel connector
-
Private blockchain
-
On-chain storage
-
Elastic search
-
Azure Off-chain storage
-
ADX search
Premium
from $8350/mo
All the Business and Enterprise features plus API integration and 3rd party data sharing
-
Single tenant
-
Sentinel connector
-
Private blockchain
-
On-chain storage
-
Elastic search
-
Azure Off-chain storage
-
ADX search
-
Public blockchain options
-
AWS & GCP Off-chain storage options
-
API Access
-
3rd party permissioned data sharing
LogLocker is easy to deploy - with experts on hand to help
Azure users with a Sentinel subscription can easily implement LogLocker.
Once you've committed to buying here's what happens next:
- Book an installation call with our engineering team
- Or, if you have immediate questions, a call with one of our team ahead of the installation meeting.
- Full details of prerequisites will be provided ahead of the installation meeting.
- The LogLocker installation will be completed within a 5 working days once meetings are confirmed and the pre-requisites are in place

Logs are ever more critical for digital compliance and security
-
Increasing cyber security costs
-
Stream lining security and compliance teams
-
Retention of high value logs for long periods
-
Increasing volumes of telemetry data
Your business wants ways to do more with less and drive value from existing security investments
For any organisation the investment in a SIEM is significant. To truly reap the benefits, it's essential to ensure that both your security and compliance teams are getting the most value out of this powerful tool. Imagine a Venn diagram where the circles of security and compliance overlap. The sweet spot in that overlap is where your SIEM should reside. It can bridge the gap between these two often-siloed functions, providing insights and efficiencies that neither team could achieve alone. By working together, your security and compliance teams can turn your SIEM into a valuable asset that protects your organization from both cyberattacks and regulatory non-compliance.
You need to avoid siloed teams by reusing skills, data and functionality to gain business efficiencies.
The disconnect between siloed security and compliance teams creates a critical blind spot. Security, focused on real-time threats, overlooks long-term compliance gaps, while compliance, chained to checklists, misses dynamic security risks. This dual vision leaves vulnerabilities unaddressed, increases audit time and fines, and ultimately weakens your overall defense. Breaking down these silos and forging a shared view through integrated tools and proactive collaboration is key to achieving resilient security and seamless compliance.
Native options are not suitable for long-term log retention being costly, unable to accommodate custom data types and lacking the preservation capabilities required.
Preserving data over vast stretches of time is a formidable hurdle. Storage technology constantly evolves, demanding data migration to survive, while physical media degrades, necessitating backups and redundancy measures. Data formats and software compatibility become obsolete, requiring costly conversions to maintain accessibility. Privacy concerns escalate with lengthy retention, demanding meticulous access control and potential anonymization. The sheer volume of data can become unwieldy, requiring efficient archiving and retrieval strategies. In short, safeguarding information against the relentless march of time is a complex juggling act demanding constant vigilance and resourcefulness.
You need tools to enable selection and filtering of logs to ensure that only those with value are processed and retained. Retaining unfiltered logs is not a sustainable option given the projected data growth and increased regulatory requirements.
The deluge of log data threatens to engulf organizations like a rising tide. Each click, sensor ping, and system event spills into the reservoir, and the torrent shows no signs of slowing. Existing tools strain under the pressure, buckling under the ever-growing weight of analysis and storage demands. Future projections paint an even bleaker picture, with data volumes set to explode exponentially. This tsunami of information threatens to drown our ability to identify critical security events and maintain regulatory compliance. Navigating this data deluge will require innovative solutions, from intelligent filtering and compression techniques to scalable storage architectures and AI-powered analysis tools. Only by riding this wave of data, not succumbing to it, can organizations unlock the valuable insights hidden within.